- OAuth 2.0 9
- OAuth 8
- Spring Security 6
- OpenID Connect 6
- Spring Boot 6
- Tutorial 5
- Keycloak 4
- Reactive 4
- Webflux 4
- React 4
- TypeScript 4
- R2DBC 4
- Microservices 4
- Hooks 3
- Kubernetes 2
- Create React App 2
- JWT 2
- JHipster 1
- Spring Framework 1
- RMI 1
- Swing 1
- Spring Cloud Gateway 1
- Jenkins X 1
- DevOps 1
- Authorization 1
- Permissions 1
- Roles 1
- Identity 1
- Scopes 1
- RBAC 1
- Authentication 1
- MongoDB 1
- NestJS 1
- Multitenancy 1
- Multi-tenant 1
- Resource Server 1
- Users 1
- User Pool 1
- Tenant 1
- Authorization Server 1
- Identity Provider 1
- Okta 1
- Auth0 1
- FusionAuth 1
- Externalized Configuration 1
- Relaxed-Binding 1
- Environement Variables 1
OAuth 2.0
Multi-tenant OAuth 2.0 Resource Servers (with Spring Security 5)

TLDR;
Merry Microservices: Part 3 ‘Policy Service’–Managing application-specific authorization based on identity and permissions

This is Part 3 of the series “Merry Microservices”
Stop overloading JWTs with permission claims

Here’s why…
Merry Microservices: Part 2 ‘UI Gateway’–A React UI served by a Spring Cloud Gateway OAuth 2.0 Client

This is Part 2 of the series “Merry Microservices”
Merry Microservices: Part 1 ‘Resource Server’–An OAuth 2.0 Resource Server with Webflux and R2DBC

This is Part 1 of the series “Merry Microservices”
Merry Microservices: An Introduction–Reactive, Full Stack and Policy-Driven on Kubernetes





Implementing Microservices Security Protocols and Patterns with Spring Security 5.2

Last month, I had the opportunity to speak with Joe Grandja at SpringOne Platform 2019 in Austin, Texas. In the talk, we break apart the pieces of an intentionally non-trivial demo to show how you can secure real-life microservices architectures with OAuth 2.0 and OpenID Connect.
HttpInvoker over OAuth 2.0 with Spring Boot 2.2
Ok, so HttpInvoker may not be the what the hipsters are using (it’s been around since 2003 or so) but there are still plenty of Java desktop applications out there communicating over RMI or EJB that could use a security boost by using OAuth 2.0.
JHipster (3.5.1) Microservices with UAA
The JHipster UAA (User Account and Authentication) server option shouldn’t be confused with cloudfoundry’s UAA – although they do similar things.
OAuth
Multi-tenant OAuth 2.0 Resource Servers (with Spring Security 5)

TLDR;
Merry Microservices: Part 3 ‘Policy Service’–Managing application-specific authorization based on identity and permissions

This is Part 3 of the series “Merry Microservices”
Merry Microservices: Part 2 ‘UI Gateway’–A React UI served by a Spring Cloud Gateway OAuth 2.0 Client

This is Part 2 of the series “Merry Microservices”
Merry Microservices: Part 1 ‘Resource Server’–An OAuth 2.0 Resource Server with Webflux and R2DBC

This is Part 1 of the series “Merry Microservices”
Merry Microservices: An Introduction–Reactive, Full Stack and Policy-Driven on Kubernetes





Implementing Microservices Security Protocols and Patterns with Spring Security 5.2

Last month, I had the opportunity to speak with Joe Grandja at SpringOne Platform 2019 in Austin, Texas. In the talk, we break apart the pieces of an intentionally non-trivial demo to show how you can secure real-life microservices architectures with OAuth 2.0 and OpenID Connect.
HttpInvoker over OAuth 2.0 with Spring Boot 2.2
Ok, so HttpInvoker may not be the what the hipsters are using (it’s been around since 2003 or so) but there are still plenty of Java desktop applications out there communicating over RMI or EJB that could use a security boost by using OAuth 2.0.
JHipster (3.5.1) Microservices with UAA
The JHipster UAA (User Account and Authentication) server option shouldn’t be confused with cloudfoundry’s UAA – although they do similar things.
Spring Security
Multi-tenant OAuth 2.0 Resource Servers (with Spring Security 5)

TLDR;
Merry Microservices: Part 3 ‘Policy Service’–Managing application-specific authorization based on identity and permissions

This is Part 3 of the series “Merry Microservices”
Merry Microservices: Part 1 ‘Resource Server’–An OAuth 2.0 Resource Server with Webflux and R2DBC

This is Part 1 of the series “Merry Microservices”
Merry Microservices: An Introduction–Reactive, Full Stack and Policy-Driven on Kubernetes





Implementing Microservices Security Protocols and Patterns with Spring Security 5.2

Last month, I had the opportunity to speak with Joe Grandja at SpringOne Platform 2019 in Austin, Texas. In the talk, we break apart the pieces of an intentionally non-trivial demo to show how you can secure real-life microservices architectures with OAuth 2.0 and OpenID Connect.
HttpInvoker over OAuth 2.0 with Spring Boot 2.2
Ok, so HttpInvoker may not be the what the hipsters are using (it’s been around since 2003 or so) but there are still plenty of Java desktop applications out there communicating over RMI or EJB that could use a security boost by using OAuth 2.0.
OpenID Connect
Cat’s Nest! OpenID Connect Authentication with NestJS, React, and MongoDB

In this post, we’ll explore how to create a NestJS back-end that handles OpenID Connect authentication for a React app that it serves up with an express-session. The session store will share the MongoDB instance that is also used for storing cats.
Merry Microservices: Part 3 ‘Policy Service’–Managing application-specific authorization based on identity and permissions

This is Part 3 of the series “Merry Microservices”
Stop overloading JWTs with permission claims

Here’s why…
Merry Microservices: Part 2 ‘UI Gateway’–A React UI served by a Spring Cloud Gateway OAuth 2.0 Client

This is Part 2 of the series “Merry Microservices”
Merry Microservices: An Introduction–Reactive, Full Stack and Policy-Driven on Kubernetes





Implementing Microservices Security Protocols and Patterns with Spring Security 5.2

Last month, I had the opportunity to speak with Joe Grandja at SpringOne Platform 2019 in Austin, Texas. In the talk, we break apart the pieces of an intentionally non-trivial demo to show how you can secure real-life microservices architectures with OAuth 2.0 and OpenID Connect.
Spring Boot
Environment Variable Generator for Spring Boot
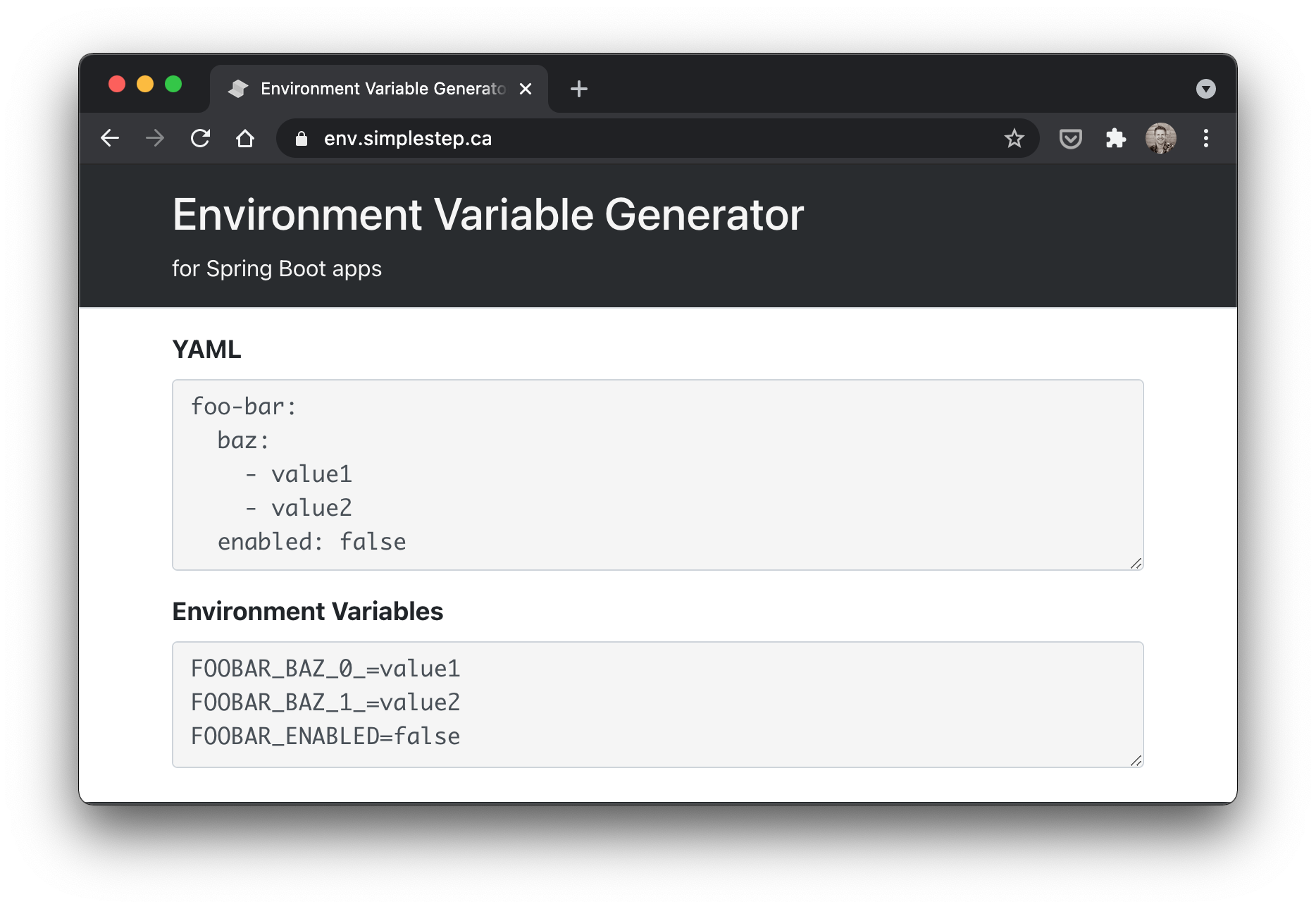
I like setting and overriding Spring Boot app configuration using environment variables.
Multi-tenant OAuth 2.0 Resource Servers (with Spring Security 5)

TLDR;
Merry Microservices: Part 3 ‘Policy Service’–Managing application-specific authorization based on identity and permissions

This is Part 3 of the series “Merry Microservices”
Merry Microservices: Part 2 ‘UI Gateway’–A React UI served by a Spring Cloud Gateway OAuth 2.0 Client

This is Part 2 of the series “Merry Microservices”
Merry Microservices: Part 1 ‘Resource Server’–An OAuth 2.0 Resource Server with Webflux and R2DBC

This is Part 1 of the series “Merry Microservices”
Merry Microservices: An Introduction–Reactive, Full Stack and Policy-Driven on Kubernetes





Tutorial
Merry Microservices: Part 3 ‘Policy Service’–Managing application-specific authorization based on identity and permissions

This is Part 3 of the series “Merry Microservices”
Merry Microservices: Part 2 ‘UI Gateway’–A React UI served by a Spring Cloud Gateway OAuth 2.0 Client

This is Part 2 of the series “Merry Microservices”
Merry Microservices: Part 1 ‘Resource Server’–An OAuth 2.0 Resource Server with Webflux and R2DBC

This is Part 1 of the series “Merry Microservices”
Merry Microservices: An Introduction–Reactive, Full Stack and Policy-Driven on Kubernetes





JHipster (3.5.1) Microservices with UAA
The JHipster UAA (User Account and Authentication) server option shouldn’t be confused with cloudfoundry’s UAA – although they do similar things.
Keycloak
Merry Microservices: Part 3 ‘Policy Service’–Managing application-specific authorization based on identity and permissions

This is Part 3 of the series “Merry Microservices”
Merry Microservices: Part 2 ‘UI Gateway’–A React UI served by a Spring Cloud Gateway OAuth 2.0 Client

This is Part 2 of the series “Merry Microservices”
Merry Microservices: Part 1 ‘Resource Server’–An OAuth 2.0 Resource Server with Webflux and R2DBC

This is Part 1 of the series “Merry Microservices”
Merry Microservices: An Introduction–Reactive, Full Stack and Policy-Driven on Kubernetes





Reactive
Merry Microservices: Part 3 ‘Policy Service’–Managing application-specific authorization based on identity and permissions

This is Part 3 of the series “Merry Microservices”
Merry Microservices: Part 2 ‘UI Gateway’–A React UI served by a Spring Cloud Gateway OAuth 2.0 Client

This is Part 2 of the series “Merry Microservices”
Merry Microservices: Part 1 ‘Resource Server’–An OAuth 2.0 Resource Server with Webflux and R2DBC

This is Part 1 of the series “Merry Microservices”
Merry Microservices: An Introduction–Reactive, Full Stack and Policy-Driven on Kubernetes





Webflux
Merry Microservices: Part 3 ‘Policy Service’–Managing application-specific authorization based on identity and permissions

This is Part 3 of the series “Merry Microservices”
Merry Microservices: Part 2 ‘UI Gateway’–A React UI served by a Spring Cloud Gateway OAuth 2.0 Client

This is Part 2 of the series “Merry Microservices”
Merry Microservices: Part 1 ‘Resource Server’–An OAuth 2.0 Resource Server with Webflux and R2DBC

This is Part 1 of the series “Merry Microservices”
Merry Microservices: An Introduction–Reactive, Full Stack and Policy-Driven on Kubernetes





React
Cat’s Nest! OpenID Connect Authentication with NestJS, React, and MongoDB

In this post, we’ll explore how to create a NestJS back-end that handles OpenID Connect authentication for a React app that it serves up with an express-session. The session store will share the MongoDB instance that is also used for storing cats.
Merry Microservices: Part 3 ‘Policy Service’–Managing application-specific authorization based on identity and permissions

This is Part 3 of the series “Merry Microservices”
Merry Microservices: Part 2 ‘UI Gateway’–A React UI served by a Spring Cloud Gateway OAuth 2.0 Client

This is Part 2 of the series “Merry Microservices”
Merry Microservices: An Introduction–Reactive, Full Stack and Policy-Driven on Kubernetes





TypeScript
Cat’s Nest! OpenID Connect Authentication with NestJS, React, and MongoDB

In this post, we’ll explore how to create a NestJS back-end that handles OpenID Connect authentication for a React app that it serves up with an express-session. The session store will share the MongoDB instance that is also used for storing cats.
Merry Microservices: Part 3 ‘Policy Service’–Managing application-specific authorization based on identity and permissions

This is Part 3 of the series “Merry Microservices”
Merry Microservices: Part 2 ‘UI Gateway’–A React UI served by a Spring Cloud Gateway OAuth 2.0 Client

This is Part 2 of the series “Merry Microservices”
Merry Microservices: An Introduction–Reactive, Full Stack and Policy-Driven on Kubernetes





R2DBC
Merry Microservices: Part 3 ‘Policy Service’–Managing application-specific authorization based on identity and permissions

This is Part 3 of the series “Merry Microservices”
Merry Microservices: Part 2 ‘UI Gateway’–A React UI served by a Spring Cloud Gateway OAuth 2.0 Client

This is Part 2 of the series “Merry Microservices”
Merry Microservices: Part 1 ‘Resource Server’–An OAuth 2.0 Resource Server with Webflux and R2DBC

This is Part 1 of the series “Merry Microservices”
Merry Microservices: An Introduction–Reactive, Full Stack and Policy-Driven on Kubernetes





Microservices
Merry Microservices: Part 3 ‘Policy Service’–Managing application-specific authorization based on identity and permissions

This is Part 3 of the series “Merry Microservices”
Merry Microservices: Part 2 ‘UI Gateway’–A React UI served by a Spring Cloud Gateway OAuth 2.0 Client

This is Part 2 of the series “Merry Microservices”
Merry Microservices: Part 1 ‘Resource Server’–An OAuth 2.0 Resource Server with Webflux and R2DBC

This is Part 1 of the series “Merry Microservices”
Merry Microservices: An Introduction–Reactive, Full Stack and Policy-Driven on Kubernetes





Hooks
Merry Microservices: Part 3 ‘Policy Service’–Managing application-specific authorization based on identity and permissions

This is Part 3 of the series “Merry Microservices”
Merry Microservices: Part 2 ‘UI Gateway’–A React UI served by a Spring Cloud Gateway OAuth 2.0 Client

This is Part 2 of the series “Merry Microservices”
Merry Microservices: An Introduction–Reactive, Full Stack and Policy-Driven on Kubernetes





Kubernetes
Environment Variable Generator for Spring Boot

I like setting and overriding Spring Boot app configuration using environment variables.
Merry Microservices: An Introduction–Reactive, Full Stack and Policy-Driven on Kubernetes





Create React App
Merry Microservices: Part 3 ‘Policy Service’–Managing application-specific authorization based on identity and permissions

This is Part 3 of the series “Merry Microservices”
Merry Microservices: Part 2 ‘UI Gateway’–A React UI served by a Spring Cloud Gateway OAuth 2.0 Client

This is Part 2 of the series “Merry Microservices”
JWT
Multi-tenant OAuth 2.0 Resource Servers (with Spring Security 5)

TLDR;
Stop overloading JWTs with permission claims

Here’s why…
JHipster
JHipster (3.5.1) Microservices with UAA
The JHipster UAA (User Account and Authentication) server option shouldn’t be confused with cloudfoundry’s UAA – although they do similar things.
Spring Framework
HttpInvoker over OAuth 2.0 with Spring Boot 2.2
Ok, so HttpInvoker may not be the what the hipsters are using (it’s been around since 2003 or so) but there are still plenty of Java desktop applications out there communicating over RMI or EJB that could use a security boost by using OAuth 2.0.
RMI
HttpInvoker over OAuth 2.0 with Spring Boot 2.2
Ok, so HttpInvoker may not be the what the hipsters are using (it’s been around since 2003 or so) but there are still plenty of Java desktop applications out there communicating over RMI or EJB that could use a security boost by using OAuth 2.0.
Swing
HttpInvoker over OAuth 2.0 with Spring Boot 2.2
Ok, so HttpInvoker may not be the what the hipsters are using (it’s been around since 2003 or so) but there are still plenty of Java desktop applications out there communicating over RMI or EJB that could use a security boost by using OAuth 2.0.
Spring Cloud Gateway
Back to Top ↑Jenkins X
Back to Top ↑DevOps
Back to Top ↑Permissions
Stop overloading JWTs with permission claims

Here’s why…
Roles
Stop overloading JWTs with permission claims

Here’s why…
Identity
Stop overloading JWTs with permission claims

Here’s why…
Scopes
Stop overloading JWTs with permission claims

Here’s why…
RBAC
Stop overloading JWTs with permission claims

Here’s why…
Authentication
Cat’s Nest! OpenID Connect Authentication with NestJS, React, and MongoDB

In this post, we’ll explore how to create a NestJS back-end that handles OpenID Connect authentication for a React app that it serves up with an express-session. The session store will share the MongoDB instance that is also used for storing cats.
MongoDB
Cat’s Nest! OpenID Connect Authentication with NestJS, React, and MongoDB

In this post, we’ll explore how to create a NestJS back-end that handles OpenID Connect authentication for a React app that it serves up with an express-session. The session store will share the MongoDB instance that is also used for storing cats.
NestJS
Cat’s Nest! OpenID Connect Authentication with NestJS, React, and MongoDB

In this post, we’ll explore how to create a NestJS back-end that handles OpenID Connect authentication for a React app that it serves up with an express-session. The session store will share the MongoDB instance that is also used for storing cats.
Multitenancy
Back to Top ↑Multi-tenant
Back to Top ↑Resource Server
Back to Top ↑Users
Back to Top ↑User Pool
Back to Top ↑Tenant
Back to Top ↑Identity Provider
Back to Top ↑Okta
Back to Top ↑Auth0
Back to Top ↑FusionAuth
Back to Top ↑Externalized Configuration
Environment Variable Generator for Spring Boot

I like setting and overriding Spring Boot app configuration using environment variables.
Relaxed-Binding
Environment Variable Generator for Spring Boot

I like setting and overriding Spring Boot app configuration using environment variables.
Environement Variables
Environment Variable Generator for Spring Boot

I like setting and overriding Spring Boot app configuration using environment variables.
